The rapid evolution of cyber crime is a major headache for security experts, whose focus has moved from prevention to live attacks. As well as thieves, asset managers are now targeted by geopolitical players, writes Alix Robertson.
A data stick found abandoned on the wall outside your building, where the smokers congregate, is best ignored. Somebody wants you to find it. They want you to plug it in. They want to access your organisation’s network and commit crime.
Victims of cyber crime in the past year range from some of the largest banks to social media sites and Sony Pictures Entertainment. Famously, it is rumoured that North Korean agents hacked Sony in revenge for The Interview, which satirised dictator Kim Jong-un.
The Heartbleed and Shellshock bugs were two of 2014’s most dangerous cyber threats. Heartbleed is thought to have affected about half a million different websites, including household names such as Google, Facebook, Instagram and YouTube, leaking memory contents and private information and allowing attackers to listen in on communications, steal data and impersonate users.
The data stick you have just plugged in may contain threats that are not simply the work of your average cyber crook. In a world of increasing geopolitical tensions, there are higher agencies at work that don’t want to steal your firm’s money, but do want to know where it’s invested.
With nation states suspected of transgressions, the arena of cybercrime is a genuine battleground. Only a small chink in your organisation’s armour is needed – and that chink could be you, picking up a data stick. What a lucky find.
ADVANCED CRIMINALS
Mark Clancy, chief information security officer at the Depository Trust & Clearing Corporation (DTCC), a US post-trade financial services company, says the cyber threat situation in the investment management world can be characterised by highly sophisticated cyber criminals.
“Historically [investment managers] didn’t have the same level of awareness of criminal threats, because they weren’t as prone to such risks as, for example, the retail payments industry,” he says.
“I think the challenge for investment managers is that they are probably less likely to be targeted by the ‘basic entry’ criminal. Instead, they are dealing with potentially the most advanced criminals, or actors led by other motivations.”
He defines different types of cyber criminals using the acronym CHEW, a term coined by Richard Clark, a former White House cyber security tsar. CHEW represents four types of attacker: criminals, who want to steal money; hacktivists, who are looking to disrupt or destroy the functioning of service; espionage actors, who are looking for secret information; or war actors, who use cyber attacks as a way of projecting force.
Clancy cites the Ukraine crisis as an example. “The industry saw an increased number of espionage actors spying on investment companies to understand what their investment plans were in Ukraine,” he says.
“Additionally, an increasing number of sanction regimes in the US, Europe and other jurisdictions and political events often then turn into either espionage activity or disruptive activity against financial institutions who are involved in that market, which is not something we had really seen before.”
BEYOND PREVENTION
The data stick is plugged in; the attack is underway. This time it was not you, but a colleague elsewhere who unwittingly instigated the threat. You, though, once the attack is detected, do have to meet with various department heads and discuss a response.
But how will you have that discussion? How do you talk about such a thing?
Matthew Martindale, director at KPMG’s cyber security practice, says there is now more of a focus on detection and response capabilities among the firms he deals with.
“We’re seeing more and more clients running simulated cyber exercises as a way of being able to practise that kind of activity happening,” he adds. “When you have your media team, your senior executives, your security team and your IT team all in the same room, can you all talk the same language?”
Deutsche Bank is one group working on this type of preparation, and Suryanshu Mishra, head of hedge funds administration business, says cyber security is central to how operations are carried out. “We regularly run surveillances on our defence and engage our technology providers to comply with evolving regulatory standards,” she says.
High-profile cases such as Heartbleed have seen firms looking to tackle cyber crime in new ways. As they begin to feel that the ever-evolving nature of cyber crime could be impossible to protect against in every circumstance, the focus is shifting towards strong capabilities for detection and repair following an attack.
Benedict Hamilton, managing director, investigations and disputes at risk solutions firm Kroll, says: “People are, by necessity, having to look more carefully at how they manage the after-effects of an incident.
“There’s quite a lot that can be done, that needs to be done, around trying to prevent the data that’s been taken being used.”
He says that simply determining whether an attack has come from outside or inside a firm, for example, is vital. “A high percentage of the cases we look at turn out to have been an insider and obviously if the insider is still inside, that needs to be managed… It can take a number of days, maybe a small number of weeks.”
To make matters worse, an attack from inside may not even be from an employee, which is where the data stick comes in again. One tactic used by hackers is to leave a USB key outside a building, which is then picked up innocently and plugged straight into a computer to see who it could belong to, immediately downloading dangerous content and exposing the whole firm to a threat.
DTCC’s Clancy says: “Prevention is ideal, but response is essential.”
He adds that if an attacker wants a target badly enough, they will figure out a way in. “You have to figure out then how to respond – both on the technical side of dealing with the incident, but also on the business and crisis management side, dealing with clients, dealing with the regulators, dealing with your investors.”
THE REGULATORS
Among the regulators, the governance and regulatory implications of cyber security are being pushed up the agenda, says Seth Berman, executive managing director of Stroz Friedberg, an investigations, intelligence and risk management company.
“UK regulators, including the Bank of England (BoE), the Prudential Regulation Authority and the Financial Conduct Authority (FCA) are actively working with the industry,” he says.
Berman says initiatives such as the BoE’s Waking Shark II exercise play a key role in heightening awareness and highlighting shortcomings in the responses to cyber attacks on institutions.
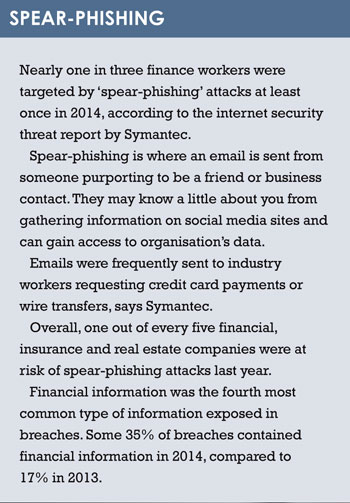 Waking Shark II tested how market participants from investment banks, financial market infrastructure providers, financial authorities and government agencies could respond to a sustained cyber attack, looking at the communication between firms and with the authorities.
Waking Shark II tested how market participants from investment banks, financial market infrastructure providers, financial authorities and government agencies could respond to a sustained cyber attack, looking at the communication between firms and with the authorities.
The BoE reported that “considerable progress has been made” since previous testing in 2011, but also identified areas to improve.
Berman says a universal set of standards for dealing with cyber security is still needed, to allow public and private-sector organisations to work better.
“We are seeing growing pressure, both in the US and at EU level, to provide greater protection for private individuals. This is likely to add further pressure on governments to legislate for mandatory data breach disclosure, which will require organisations to strengthen their own cyber resilience and response plans,” he adds.
The FCA says it is widely engaged with a number of stakeholders on cyber issues, and has established a large network of engagements and contacts to “leverage a wide range of skills”.
It tells Funds Europe: “We are focused on ensuring the right outcomes based on our three operational objectives. We expect firms to provide redress for consumers impacted by cyber crime – consumers should not lose out as a result of cyber crime.”
Michael Soppitt, a director in the digital risk and information security practice at financial services consultancy Parker Fitzgerald, suggests there is still some way to go for the regulators.
“The digital revolution has just outstripped anyone’s expectations of how quickly that could happen,” he says. “As a result, the cyber threat itself has also grown exponentially and regulators actually have been left caught out, to be honest, in many respects.
”I think there’s a lack of a joined-up approach to this at the moment and that’s a major challenge for asset managers and anyone across the financial services industry.”
This could be an opportunity, he says, for proactive firms who have prepared for cyber attacks to demonstrate their capabilities. “The regulators are expecting organisations to engage with them and agree what is best. It’s actually an opportunity for many institutions to differentiate themselves and to forge ahead.”
While some firms are ready to engage in high-level discussions on how to take cyber security forward, for many the focus is still on making sure the basics are in place and employees understand what they are up against.
Luke Beeson, vice president, security UK and global banking and financial markets at BT, says implementing basic security controls is a good place to start when confronting cyber crime, and firms should ensure they maintain and update features such as antivirus software, firewalls and proxy servers.
It is also important to ensure that employees at all levels are educated about the risks.
“Sometimes you can have all the necessary defence mechanisms in place, but user error, such as someone unwittingly clicking on a link, can trigger an ‘in’ that’s enough for the attack to start and proliferate,” he says.
Senior executives need to know more too. A recent KPMG survey of 133 global institutional investors with over $3 trillion (€2.7 trillion) under management found that investors believe fewer than half (43%) of the boards of companies they invest in have adequate skills to manage cyber risk.
Malcolm Marshall, global leader of KPMG’s cyber security practice, says board members need to understand and approach cyber security as a business risk issue, ”not just a problem for IT”.
Hamilton at Kroll says that among even some of the larger players in financial services, there are “dangerous levels of ignorance” when it comes to cyber security, which can result in the loss of hundreds of thousands if not millions of pounds.
He adds that a key problem is misunderstanding what sort of data is of value to attackers. Stolen credit card details used to be of high value because they could be sold on the dark web. But today, access to a valid social media address is more sought after.
“It’s important for companies to think about the particular threats that they face, given what they do,” he says.
Parker Fitzgerald’s Soppitt compares the situation to siege warfare. A firm must understand what its ‘crown jewels’ are when it comes to protecting business-critical information and ensure they are kept safe.
“Over the past year we’ve seen about 13 fund groups have sensitive client data stolen. It’s almost always customer account information, which is a particularly risky asset for asset managers.
“When it comes to the protection of data, the question is, what are your key assets as an organisation?”
Firms are frequently too preoccupied with protecting the perimeter of their organisation, he says, building higher walls and expecting nobody to get in.
“In a digital world, boundaries don’t exist like that…organisations need to understand how the world has changed.”
He adds: “There’s incredible investment in cyber security at the moment, and organisations can quite literally fritter away millions and millions of pounds on the wrong thing.”
The experience of one large banking and financial services company that was attacked in late 2014 illustrates the point. “When they were breached they had just said that they were going to spend $250 million on security,” Soppitt says.
“When they got breached, they said: ‘Actually, now we’re going to spend $500 million on security.’
“You can spend as much as you want, but if you’re not spending it in the right places, it’s not going to help you.”
The landscape of cyber crime is constantly evolving. A variety of areas need to be addressed, from prevention to detection and repair. If firms want to establish themselves as worthy adversaries to the unknown armies of cyber criminals, it seems they must take a holistic approach.
Soppitt’s advice to asset management firms is simple: “Security is a process and not a product.”
©2015 funds europe





